
"It is
impossible for ideas to compete in the marketplace if no forum for
their presentation is provided or available." � �Thomas Mann, 1896
Secure Identity
Management
A Better Solution for
Secure High-Volume Key Management
Contributed by SafeNet Corporation
Introduction
From VPNs (Virtual Private Networks) protecting corporate communications to the widespread adoption of digital signatures validating electronic transactions, the demand for secure electronic transactions has grown in step with an increasingly wired world. Traditionally, Public Key Infrastructure (PKI) based applications have provided the building blocks for many security solutions. With flexible capabilities ranging from encryption to maintain privacy, to digital signatures used to prove identity. PKI-based solutions have demonstrated that the technology can work successfully for thousands of users.
However, as solutions scale upwards to support larger numbers of users, the process of safeguarding and managing large numbers of cryptographic keys becomes more difficult. While dedicated cryptographic HSMs (Hardware Security Modules) provide a high degree of assurance due to the physical and electronic security incorporated into their design, they are ill suited to store thousands, or millions, of keys. In contrast, database management software (DBMS) is capable of managing millions of unique pieces of data (keys in this example) but cannot offer the high degree of security inherent in HSM solutions.
The need for a solution that incorporates the high-security features of a traditional HSM while respecting the flexibility and control offered by a DBMS is clearly evident. To meet these demands, SafeNet created Secure Identity Management (SIM), a secure, high-volume key management solution, as part of its Ultimate Trust Security Platform (UTSP). SIM, in conjunction with a third-party DBMS like Oracle or Microsoft SQL, delivers a solution that can scale to meet the demands of PKI-based solutions requiring the management of large numbers of Private Keys while maintaining the levels of security offered by HSM based solutions.
The
SafeNet Ultimate Trust Security Platform
The SafeNet UTSP is an Ethernet
attached,
multipurpose security
platform designed to
provide security solution developers
with powerful, flexible,
network
shareable
hardware
security for
their
applications. Unlike a general
purpose
computer, the UTSP has
been
designed from the ground up
to
provide the highest levels of
physical,
electronic, and operational
security.
The UTSP is built
around
an integrated SafeNet K3
Cryptographic
Engine, a dedicated
FIPS
140-2 Level 3 validated
(pending)
high-performance HSM,
offering
SafeNet� proven hardware
key
management and capable of
processing
over 1200 digital signatures
per
second. The UTSP also
features
PKI secured software
updates,
remote network monitoring
and
management, optional
Secure
Authentication and Access Control (SAAC) with 2-factor authentication, and
support for
all
standard cryptographic APIs to permit rapid development and integration into
security applications on
a
broad range of platforms.
The UTSP�s dedicated HSM, the K3 Cryptographic Engine, coupled with its network connectivity, make it ideal for applications where large numbers of keys must be managed, stored, and used, such as secure email, high-volume digital signing, or digital identity solutions (e.g. smartcards). In addition, the SafeNet UTSP also features SIM as an optional configuration for solutions requiring the secure management of large volumes of keys or digital identities.
The Need for Private Key Security
PKI-based applications rely on asymmetrical cryptographic processes to create digital identities used during encryption, decryption, and digital signing. Asymmetrical cryptography uses a set of mathematically related cryptographic keys (called a key pair), consisting of a Public Key and a Private Key, to perform cryptographic operations. A user�s Public Key is freely distributed and used to encrypt messages sent to the user; the Private Key is kept secret, and used to decrypt and digitally sign messages. As the name implies, the Private Key must be kept secret and known only to its owner - otherwise, someone else with knowledge of a user�s Private key could surreptitiously snoop on private communications or even masquerade as the legitimate Private Key owner.
For this reason, Private Keys, particularly ones corresponding to high-security or high-value operations, are protected with specialized, often elaborate hardware and operational procedures, ranging from an individual�s smartcard on the low-end of the spectrum, to highly secure bunkers containing specialized HSMs for valuable corporate and government Private Keys.
However, the demands for physical security can complicate matters in an electronic world. Smartcards require corresponding smartcard readers and other attendant hardware to operate, preventing widespread, cost-effective adoption. Hardware devices, such as smartcards containing Private Keys, can be lost or misplaced, rendering email and data unreadable, as their owner no longer has the digital key to decrypt them. Online services, like banking and web-based email, have difficulty deploying large numbers of Private Keys electronically to users due to the cost of widely deploying hardware or the lack of security inherent in software solutions.
Key Wrapping
While HSMs are highly effective for protecting sensitive Private Keys, it is not practical for everyone who uses PKI-based solutions to deploy a dedicated HSM device. Additionally, some organizations may wish to use the HSM to generate new Private Keys (for smartcards, for example) but are unable to store the new keys locally on the HSM due to limited storage space, or lack of portability. To allow Private Keys to be transferred from one HSM to another (for example, to move a new Private Key from an issuing HSM to a smartcard), or to save a Private Key as a digital file, the Private Key must go through a secure process called Key Wrapping. During the Key Wrapping Process, a Private Key on the HSM is encrypted in a cryptographic �wrapper� and then exported to another device or file.
Key Wrapping Techniques
Key Wrapping is the process whereby a Private Key is exported, or �wrapped off �, of the HSM as an encrypted electronic file. This encrypted file, containing the Private Key, can then be transferred to another device, or even stored electronically as a file on a computer.
The key wrapping operation has 3 steps:
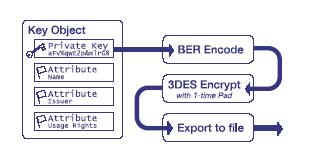
Encrypt with 3DES One-Time Pad Cipher � Next, the encoded Private Key Data is encrypted using a one-time pad cipher. A one-time pad is a unique encryption key that is used only once. This key is generated by the HSM to produce the keying material used to perform a 3DES (triple-DES) encryption turn on the encoded data.
Export Wrapped Key � The 3DES encrypted data is then exported off of the HSM where it can be transferred to a file or imported into an application.
The Problem With Key Wrapping
Key Wrapping appears to offer a solution to the problem of being able to generate and store large numbers of keys; keys can be generated within the confines of the HSM and, presumably, safely exported to an external application for use, continuously protected by a strong one-time pad 3DES cryptographic wrapper. However, on closer inspection, several weaknesses can be exposed in this system.
With Key Wrapping, only the Private Key data is wrapped, ignoring all the other attribute flags present in the Key Object. While some of the attribute flags are present strictly for administrative purposes, like the Name of the certificate, other flags, like the �Usage� attribute flag, define how a Private Key can be used, and are more important. The following scenario demonstrates an example of how this can be abused:
A Key Object flagged with a �decrypt only� attribute, is wrapped and exported from an HSM; later, an unscrupulous system administrator imports the wrapped key back onto the HSM. However, the imported key is now devoid of its original �decrypt only� attribute flag. By taking this �de-flagged� Private Key, the system administrator can define new attribute flags, for example, setting the usage flag on the naked key to �decrypt and sign� instead of the �decrypt only� flag from its parent. In this way, the system administrator can easily change attribute flags associated with a given Private Key, side-stepping existing administrative safeguards.
Another potential weakness present in this wrapping model is the ability to export the 3DES-wrapping key as a separate entity. This requires no special hacking - the capability is specified as part of the PKCS#11 standard. In this way, it is possible to export both the Private Key and the 3DES key used to wrap it, allowing an unscrupulous operator to gain access to the Private Key.
To overcome these weaknesses, SafeNet created SIM to provide a new, more robust, wrapping process that maintains the integrity of the entire key object and prevents the wrapping keys from ever being exposed outside the HSM.
How Secure Identity Management Works
Unlike the key wrapping techniques described earlier, SIM takes a different, more secure approach to the management of both HSM wrapping keys and the process whereby Private Keys that are exported.
There are 4 major steps performed during the
SIM export process:1. Key Object Preparation
2. Integrity Check
3. Key Masking
4. Wrapped Key Export
Key Object Preparation
� Starting with the original Key Object, SIM �flattens� the entire Key Object, including all the attribute flags, into one large data string. This allows the entire Key Object, including the Private Key and all attribute flags present within the Key Object, to remain intact during the export process.Integrity Check � Next, the flattened Key Object data string is subjected to a multi-step integrity check procedure. This integrity check can be used later to detect corruption or tampering with the Key Object during its storage in an external data source. Together, the flattened Key Object and its related integrity check data, are combined to form the input data string for the Key Masking process.
Key Masking � The Key Object, with its related integrity check data, is next processed through a multi-stage encryption process called Key Masking. Key Masking relies on multiple cryptographic processes and combines several unique one-time encryption keys to form an extremely strong cryptographic wrapper around the entire Key Object, not just the Private Key.
At the center of the Key Masking operation is the Masking Key, a unique 512-bit key that is stored within the confines of the UTSP�s integrated K3 Cryptographic Engine, a dedicated high-performance FIPS 140-2 Level 3 validated HSM. First, the UTSP seeds its pseudo random number generator (PRNG) with a derivative of the Masking Key to create a masking function over the Key Object Data. Next, the K3 Cryptographic Engine�s Hardware Random Number Generator (HRNG) generates a one-time pad used as the basis for an AES 256-bit encryption key. This Key is then used to encrypt the Key Object data in a secure cryptographic wrapper.
It is important to note that unlike other wrapping procedures, the key used to encrypt the wrapper, in this case, the Masking Key, is never exposed outside of the confines of the HSM.
Wrapped Key Export � Finally, the one-time AES key is encrypted using a derivative of the Masking Key. The resulting encrypted AES key data is appended to the previously encrypted Key Object data. The resulting file is now safe to export to the HSM�s host applications, where the encrypted data can be stored in a database until needed.
SIM Benefits
With SIM, SafeNet protects and preserves the entire key object during the export process, rather than only the Private Key itself. This is beneficial since all the attribute flags of the Private Key are maintained throughout the SIM process thereby preventing modification or tampering to both the Private Key and its attribute flags. The inclusion of this attribute flag meta data along with the Private Key itself makes the resultant data richer and more portable, while preventing the reassignment of new attributes to �naked� wrapped keys after decryption.
The added integrity checks included as part of the SIM export process ensure that data cannot be altered without detection, eliminating the possibility of undetected data manipulation when encrypted SIM keys are exported or stored outside of an HSM. Data that fails the integrity checks during the decryption process is ignored, preventing the insertion of illicit data into the SIM process.
SIM also maintains the SIM decryption (Masking Key) key within hardware at all times. Unlike a traditional key wrap where standard PKCS#11 calls can be used to extract the 3DES wrapping key to a file, or worse yet, allow a compromised key to be injected into the HSM for use as a wrapping key, the SIM Masking Key can neither be created nor exposed outside of the HSM.
SIM System Deployment
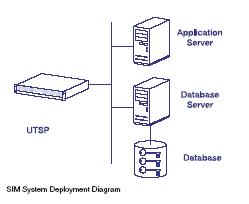
The SafeNet Luna SA provides the cryptographic security backbone for SIM.
The integrated K3 Cryptographic Engine is a full-featured HSM designed to protect the Masking Key used to derive the keying material applied during the Key Masking process.
The K3 Cryptographic Engine�s dedicated cryptographic processors also provide the cryptographic performance to generate, encrypt, and decrypt large numbers of SIM keys during operation, in addition to providing cryptographic acceleration during the actual use of SIM keys (to digitally sign a document, for example). By offloading the processor-intensive cryptographic chores, the SafeNet UTSP prevents bottlenecks at the Application or Database Servers while providing the assurance of hardware secured key management.
The Application Server hosts the actual application itself, for example a secure email server or a transaction server that requires digitally signed transaction records. The Application itself is integrated with the UTSP through standard cryptographic APIs, such as Java JCA, PKCS#11, or Microsoft CryptoAPI, so that all calls for Private Keys retrieve the necessary encrypted SIM key from the database and deliver it to the Luna SA for decryption and use.
The Database Server provides the storage and management facility for the Application, allowing large numbers of SIM keys to be stored and retrieved by the host Application. The Database server also provides the infrastructure for backup and recovery of SIM keys.
Together, each component adds core capabilities to the overall system functionality. The Luna SA secures Private Key data through its built-in HSM and SIM processes while providing increased Application performance by offloading cryptographic operations from the application server. Freed from the burden of performing cryptographic processing, the Application Server provides dedicated transaction handling to optimize user response times. The Database Server provides efficient storage and management of the encrypted SIM keys, permitting the system to manage and retrieve thousands, or even millions, of keys as required by the application.
Example SIM Application
One example of an application suited to SIM is an email server offering digital signing. Because an email server may host hundreds of thousands of clients and users accessing email from a variety of locations, it is not practical or cost effective to use smartcards or other tokens to store the users� keys. Instead, the mail server use SIM to store and manage keys on behalf of the users - this way, the users can still have access to their keys while travelling or while using another computer.
Each user is issued a key that is generated in hardware by the UTSP�s integrated HSM. This new key is then wrapped using the SIM process and exported to the mail server�s key database. When the user wishes to sign a document, the mail server retrieves the user�s encrypted SIM key from the database and passes it to the UTSP for decryption. Inside the UTSP�s HSM, the wrapped key is decrypted using the secret Masking Key, its integrity is verified, and its usage attributes are checked before the HSM signs a document with it. Because the user�s unencrypted Private Keys are never exposed outside of the HSM, the user enjoys the benefits of an HSM�s security without having to carry around a physical token. The mail server is freed from performing processor intensive cryptographic operations, improving application response time and performance. Additionally, because keys are stored and managed with a database, a DBMS handles the sundry tasks of storing, managing, retrieving, and backing up large amounts of key data.
Conclusion
With the introduction of SIM, SafeNet offers a new, more secure method for handling the demands of high volume key management necessary for the safe and secure storage of large numbers of digital identities. SIM is ideally suited for applications requiring hardware protection for large numbers of keys, or the maintenance of users� Private Keys securely in the software domain, applications where traditional software or HSM solutions are too limited in scale to address large numbers of users, too cumbersome to deploy and manage, or too insecure to protect valuable information assets.
SIM represents a dramatic security increase over existing key export models by retaining all Key Object data, providing a built-in data integrity check, increasing cryptographic security with stronger multi-stage encryption, and maintaining encryption keys exclusively within hardware.
By offering the ability to export the entire key object, rather than just the Private Key portion of a Key Object, SIM greatly increases the portability of SIM key objects over traditionally wrapped keys while preventing misuse of raw, un-flagged, private key data. The built-in integrity check within SIM provide a mechanism to maintain the validity of data in the face of potential corruption or tampering. SIM increases the security of exported Private Keys with a multi-stage, multi-algorithm encryption process that is much stronger than the 3DES algorithm currently in use. Finally, during the SIM process, the HSM�s private wrapping key (Masking Key) is never exposed outside the confines of the HSM, reducing the risk of compromise from the HSM�s private keys falling into the wrong hands.
Nothing you read in The Business Forum Journal should ever be construed to be the opinion of, statements condoned by, or advice from, The Business Forum Institute, its staff, workers, officers, members, directors, sponsors or shareholders. We pass no opinion whatsoever on the content of what we publish, nor do we accept any responsibility for the claims, or any of the statements made, within anything published herein. We merely aim to provide an academic forum and an information sourcing vehicle for the benefit of the business and the academic communities of the Pacific States of America and the World. Therefore, readers must always determine for themselves where the statistics, comments, statements and advice that are published herein are gained from and act, or not act, upon such entirely and always at their own risk. We accept absolutely no liability whatsoever, nor take any responsibility for what anyone does, or does not do, based upon what is published herein, or information gained through the use of links to other web sites included herein. Please refer to our: legal disclaimerEditorial Policy:
The Business Forum
Beverly Hills, California, United States of AmericaEmail: [email protected]
Graphics by DawsonDesign
Webmaster: bruceclay.com