
"It is
impossible for ideas to compete in the marketplace if no forum for
their presentation is provided or available." � �Thomas Mann, 1896
Network Access Control Technologies
By Richard Langston
Contributed by Sygate Technologies, Inc.
Summary
Today, businesses must face the very real threat of their systems being compromised by misuse, misconfiguration and malicious access. In fact, Gartner estimates that 20 percent of managed systems are already compromised. Add to that their estimate that 20 percent of systems on corporate networks are entirely unmanaged and it becomes clear that most enterprises are vulnerable to loss of productivity, leakage of confidential information, and other expensive (and potentially embarrassing) abuse.
Network Access Control is a process designed to reduce security incidents and increase compliance by enforcing IT security policies as a prerequisite for network access. Although the term “Network Access Control” is a newly-defined category, Sygate Technologies, Inc., has been a leader in policy enforcement for years, blazing the trail with the first implementations of VPN (IPSec and SSL), LAN (802.1x), and agent Self-Enforcement techniques for Network Access Control.
Today, Sygate has many large enterprise customers who have deployed complete NAC solutions. NAC solutions require multiple enforcement methods and policy flexibility to cover the entire enterprise network. Customers should carefully assess their environments and requirements against each possible solution. As an innovator in NAC solutions, Sygate provides the most comprehensive and flexible set of options for deploying Network Access Control to best fit the needs of your enterprise.
Several consortiums and standards have emerged that promise to create NAC standards for network infrastructure, authentication, endpoint security, and policy management vendors to integrate with. Chief among these are Cisco’s Network Admission Control (NAC), Microsoft’s Network Access Protection (NAP), and the Trusted Computing Group’s Trusted Network Connect (TNC) initiatives. Sygate is an active participant in each of these efforts and will offer customers the capability of leveraging these standards to perform NAC functions. Sygate is in a unique position to simplify NAC customer implementations by unifying essential NAC policies in one place: the Sygate Management Server. Customers who deploy Sygate Secure Enterprise and one of Sygate’s current enforcement methods — Self-Enforcement, VPN Enforcement, 802.1x, API Enforcement — can seamlessly integrate with these new technologies as they become available for general use in the LAN.
Introduction
Enterprises today face many IT challenges. Key among these are combating ever more frequent security incidents and striving to maintain regulatory compliance. Misuse, misconfiguration, and malicious access to critical corporate systems have reached epidemic levels. A common thread among these challenges is the need to ensure protection and control of the endpoint. Many security incidents, for example, are caused by simple desktop misconfigurations and out-of-date security patches. Similarly, controlling which applications can run on the endpoint (and where) goes a long way toward meeting regulatory challenges.
While existing technology such as patch and vulnerability management systems give IT reactive ways to keep systems up-to-date, they do not address a key element of any real solution: keeping systems that are not up-to-date, or are otherwise non-compliant, off the network altogether, and creating a way to repair them without the intervention of IT desktop support or the help desk.
Network Access Control technologies address this problem by auditing the security stance of endpoints before they connect and making appropriate updates before there is a connection to the standard corporate network. This keeps worms and viruses off the network and also allows enforcement of application level security policy.
Deploying even the simplest NAC solutions requires a great deal of planning and ties together components from many different vendors. Sygate Technologies, Inc. , has been a pioneer in the NAC space, releasing the first product with NAC capabilities in 2002. Since these first products, which were targeted at protecting corporate LANs from non-compliant VPN users, Sygate has expanded its NAC solutions to include On-Demand and LAN-based solutions. This experience building proven customer solutions has given Sygate a unique perspective on how to build working, real-world NAC solutions that realize the promise of the technology: significant improvements in network availability and resiliency in the face of security incidents.
In this paper, we will look at the theory behind this technology, including The Gartner Group’s definition of the NAC solution. We will also examine Sygate’s Compliance on Contact, Cisco’s Network Admission Control, Microsoft’s Network Access Protection, and the Trusted Computing Group’s open platform for NAC in detail.
What is Network Access Control?
Several industry analysts have weighed in on NAC technology, each with a different set of terminology and slightly different definitions of what NAC solutions should entail. For example, Forrester has coined “Network Quarantine”, while Meta uses “Endpoint Access Control.” Gartner has also created a reference design for Network Access Control. This design is really a continuous process for evaluating endpoints, mitigating security problems, admitting systems to the network, and monitoring them on an ongoing basis for compliance with a set of globally-maintained policies.
Since the Gartner framework is one of the most complete, it is worth looking at the process it defines and also the pieces that are required to make NAC work. Gartner’s NAC process starts with the definition of security policy. Policies outline the security configurations that administrators wish to enforce as a prerequisite for network access. These policies can include any system or third-party software configurations, depending on the needs of the organization.
Typical examples of policies that most enterprises will want to enforce include verification that operating system security patches are up-to-date, antivirus software is running and signature definitions are up-to-date, and that endpoint firewall software is running and properly configured. Administrators may also want to do a malware scan to verify that there is no malware on the system.
Once policies have been created, a baseline is used to compare systems connecting to the network with the configured policy. An important consideration is that this baseline evaluation must be run regardless of how systems connect to the network. LAN, WAN, Wireless, IPSec, and SSL VPNs must all perform this baseline evaluation in order to secure the network.
Based on the results of the baseline, Access Control is used to give the connecting system the appropriate level of network access. For example, a system that is in compliance with the baseline will receive full access to the network. Systems that are not compliant will either be blocked outright with no access to the network, or will be sent into a quarantine level of network access for the purpose of mitigation (remediation) to bring the system into compliance. In order for NAC to be of value, the mitigation process must be automated. In other words, systems need to be brought into compliance with security policy without calls to the help desk.
Once systems have undergone mitigation and been admitted to the network, a monitoring technology needs to be used to ensure that they remain in compliance and do not exhibit anomalous behavior. Systems exhibiting anomalous behavior must be sent into a containment (quarantine) area until they can be repaired.
Therefore, Network Access Control solutions need to:
1. Evaluate the security state of a system or user as it connects to the network;
2. Monitor the security state of systems that are already connected;
3. Implement network access and system remediation policies based on the state of the system.
In addition to Gartner’s NAC framework capabilities, real-world NAC solutions need several more characteristics in order to meet the needs of today’s large enterprises. These include:
Shipping support for multiple access methods (remote access VPN IPSec, dialup, SSL VPN, wireless, LAN, DHCP, 802.1x, web access, etc.). In order to be successful, a NAC rollout must be able to guard all of the entrances to the corporate network from day one. Locking the front door won’t keep anyone out if the back door is wide open.
Enterprise-class scalability and manageability, including disaster recovery, redundancy, and segregation of management functions to regional teams.
Flexible deployment strategies, with proven results. Features such as “learning mode” that allow NAC solutions to be first deployed in an audit mode significantly reduce the pain caused by introduction of these new IT practices.
Extensible, customizable policies that allow administrators to create their own custom NAC rules without requiring help from their NAC vendor.
Robust location-based policies that are needed to reduce the impact of NAC on the work practices of end users.
Multi-vendor, open solution that supports various technology components existing in enterprise networks today and for years to come (such as VoIP, WLAN, etc.)
Sygate Compliance on Contact
Sygate is an early leader in Network Access Control solutions. Sygate’s Compliance on Contact technology delivers the industry’s widest range of NAC solution options available today.
The intense focus on NAC technologies has also led to other NAC efforts. Operating system and network vendors Cisco and Microsoft have weighed in with their own NAC architectures, and the industry as a whole has created the first set of standards for truly open NAC architectures in the form of the Trusted Computing Group’s Trusted Network Connect (TNC) initiative. Sygate is active in all of these efforts, and is incorporating product support for each of these enforcement architectures.
Using the Sygate Management Server, IT administrators can centrally manage their network access policies. These policies include built-in checks for well-known antivirus software, personal firewalls, anti-spyware, operating systems, and security patches. There is also an advanced toolbox for creating custom checks based on files found on the system, applications that are running, registry settings, file dates and checksums, and the like.
Adaptive Policies allow different policies to be enforced, depending on what type of network connection the user is trying to use: users connecting via IPSec VPN could be required to have a higher level of NAC compliance, since they are exposed to the public network. For example, an organization can make policies requiring that any Windows 2000 system have service pack 4, any Windows XP system have service pack 2, and that all systems be running McAfee Antivirus with up-to-date signature files. Or, they could mandate all of the above, plus other custom security applications and a custom registry key that is set by IT.
Once policies are created, they are enforced on network connect by Compliance on Contact.
Compliance on Contact enforces compliance at each
connection point in the corporate network. This includes performing the full set
of NAC baseline checks when users connect to the corporate network via IPSec
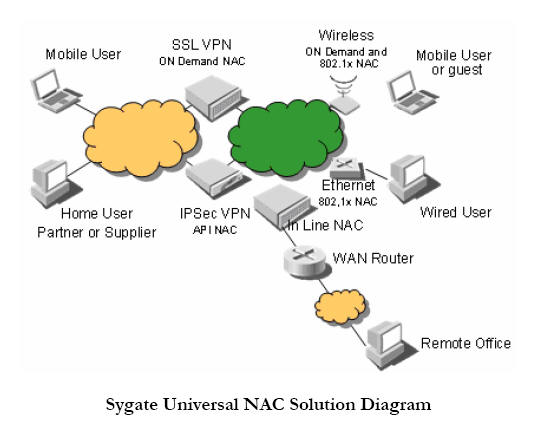
VPN, SSL VPN, wired Ethernet, and wireless Ethernet. The figure labeled “Sygate
Universal NAC Solution,” illustrates network connection points and the methods
used by Compliance on Contact. This is Gartner’s baseline step. See the figure
below for a look at supported and tested network infrastructure
vendors.
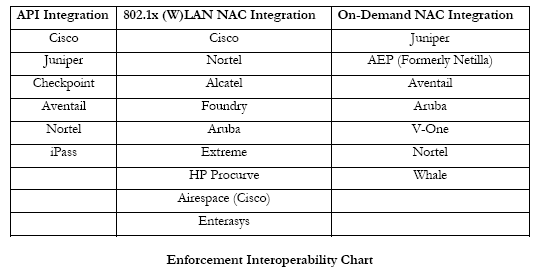
Once the baseline is performed, Access Control is the next step in the solution. If systems are in compliance with policy, they are permitted on the network. The techniques used for access control will vary depending upon the type of connection. The Sygate agent will automatically perform a preconfigured operation to bring the system into compliance without user intervention. Once updated, the system will repeat the process and, since it is in compliance, will get access to the corporate network. See the figure below for a complete look at the process.
Compliance on Contact continues to monitor the status of the client, and will take action to contain the system if it falls out of compliance.
Sygate uses four different
technologies to accomplish the complete NAC solution. When users connect into
the network by IPSec VPN, an API is used to communicate to the Sygate Security
Agent installed on the remote system and determine if the system is in
conformance with policy. In order for this NAC method to work, the IPSec VPN
gateway must support Sygate’s Universal Enforcement API. Sygate works with most
VPN vendors to ensure compatibility with this API, including Cisco, Nortel,
Juniper, Aventail, AEP, and Array Networks. In situations where the VPN gateway
does not support the Sygate API, Sygate’s in-line Gateway Enforcer can be
inserted into the network behind the VPN to perform this function.
The introduction of SSL VPNs created the need for an additional NAC component that was web-oriented. To meet this need, Sygate developed the Sygate On-Demand Agent (SODA). SODA includes a Java-delivered, on-demand NAC component that can evaluate the policy status of a system without the need for a pre-installed, permanently-resident agent. SSL VPN gateways can deliver this agent via their web authentication page and ensure that systems are compliant before they are allowed access to the corporate resources controlled by the gateway. Juniper, Array Networks, Netilla, and Aventail are a few of the SSL VPN vendors that include SODA-based NAC support in their products.
In addition to VPN access, administrators may also want to control access to critical network resources, such as the data center or WAN links to remote offices. Sygate’s in-line Gateway Enforcer was designed to do just that. It functions by intercepting traffic and permitting it through based on configured policy. If systems are not compliant with the policy, they can be prohibited from accessing network resources that are behind the enforcer. See below for a look at Sygate’s history of innovation in NAC technologies.
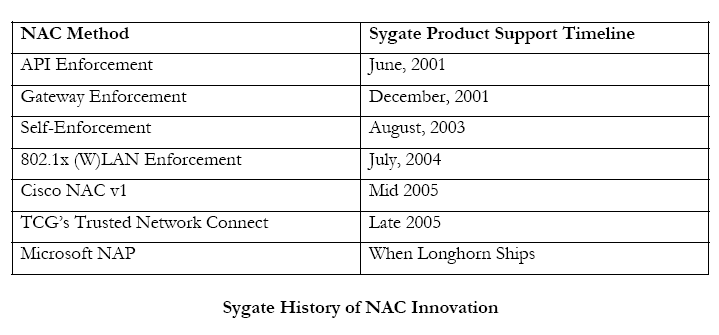
Sygate released one of the first LAN-based Network Access Control technologies in June 2004. This enhancement to Sygate Secure Enterprise (SSE), the industry-leading endpoint protection product, leverages the IEEE’s 802.1x Admission Control Protocol, which is supported by nearly all wired and wireless Ethernet switch makers. SSE uses this link-level protocol to evaluate endpoint compliance, provide automatic problem remediation, and admit compliant systems onto the corporate net.
During LAN enforcement, the Sygate Security Agent on the endpoint uses 802.1x to transmit compliance information to the network switch, which relays it to a Sygate LAN Enforcer. This LAN Enforcer functions as a RADIUS proxy, verifying the compliance information and optionally consulting with a RADIUS server to verify usernames and passwords or multifactor authentication.
If the system is not in compliance, LAN Enforcer will place it in a quarantine network where it can be remediated without impacting any of the systems that are in compliance with policy. Once Sygate has performed the automated remediation function, the 802.1x protocol will attempt to re-authenticate the user. Since they are now compliant, access to the network will be given, as the figure below shows.
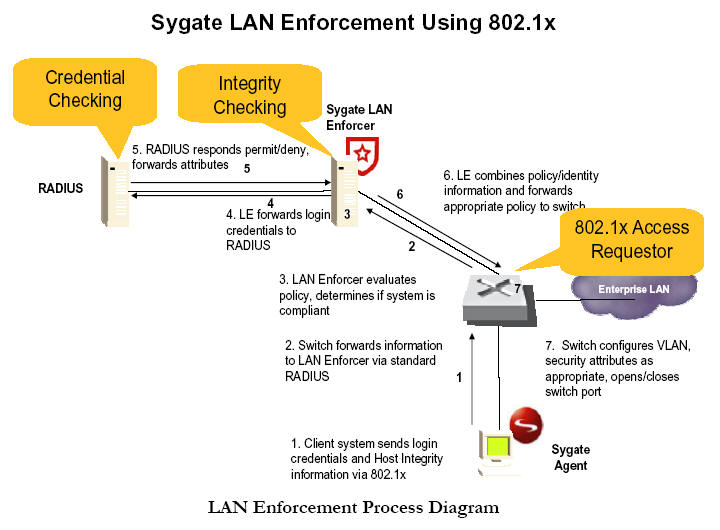
One of the major strengths of Sygate’s Compliance on Contact is its ability to
securely manage the compliance of many different components — antivirus,
patches, applications, and more — from a single console. Further, Sygate
performs this functionality with the use of a single desktop or On-Demand agent,
performing NAC functions and providing a robust endpoint firewall and intrusion
prevention system, which lock down the desktop even further. Customers running
Sygate Security Agent can simply enable NAC capabilities in their central policy
management servers and add appropriate Enforcers to their network.
Cisco Network Admission Control
In 2004, Cisco announced an initiative called “Cisco Network Admission Control,” with an architectural framework and roadmap they are marching towards, releasing functionality in several phases over several years. Within the Network Admission Control initiative, Cisco has focused on building protocols and interfaces that can be used by multiple vendors to provide a complete NAC solution. As such, the Cisco Network Admission Control framework requires software from several different vendors to build a complete solution.
One major difference between Sygate’s architecture and Cisco NAC is support for various network infrastructure vendors, as Cisco NAC only works with Cisco network hardware. In the first phase released in 2004 , NAC support is available for the router products, providing a subset of the functionality in Sygate Gateway Enforcer. Administrators using Sygate Security Agent now have two options for enforcing policies at their gateways: depending on the level of functionality required, they can either deploy Sygate Gateway Enforcer or a Cisco NAC-enabled router. To use the NAC-enabled router they would require two extra software components: first, they would need to deploy Cisco Trust Agent (CTA) on all their endpoints (CTA), available today on Windows 2000 and XP platforms, is similar to the Sygate Host Integrity Agent and is responsible for communication with Cisco’s NAC-enabled router, reporting the security status of the endpoint as reported in turn by third-party security agents, such as the Sygate Security Agent); second, they need Cisco’s AAA server, “ACS.” ACS authenticates the endpoints and brokers any communication required with backend third-party policy servers to verify the endpoint’s security policy compliance. In phase 2, Cisco plans to extend these capabilities to reach their layer 2 switches and other network components in 2005.
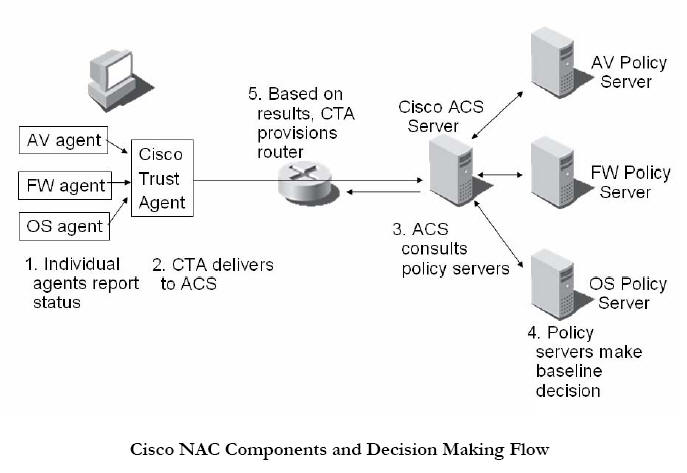
Cisco’s NAC architecture encompasses elements that reside on the client PC, a network transmission protocol the client uses to communicate with Cisco’s ACS server, a server-to-server protocol, and a set of messages that ACS uses to provision the switch.
As mentioned above, on the client side, Cisco’s architecture consists of a “posture assessment” agent called the Cisco Trust Agent, which requires third-party plug-ins to report the status of the endpoints. CTA cannot enforce the policies if the system (like a laptop) is connecting to a non-NAC-enabled network. Each plug-in is created by an individual security or OS vendor (like Sygate) and separately reports its status. A separate plug-in may be needed for each individual security component: antivirus, anti-spyware, host IDS, patch, endpoint firewall, etc.
The decision-making component of
Cisco NAC is similarly distributed. The CTA reports its information to Cisco’s
ACS RADIUS server. This server, in turn, delivers the security information
received from the individual plug-ins to corresponding policy servers in the
back end: one each for antivirus, firewall, patch, etc. ACS then collects these
responses and makes an ultimate policy decision about what level of network
access to give the endpoint. Remediation is the responsibility of the
third-party security agents. The figure labeled “Cisco NAC Components and
Decision Making Flow" illustrates version 1 of Cisco’s NAC.
Cisco’s decentralized approach has both advantages and disadvantages for
administrators.
The flexibility of allowing each individual agent to report its actual security status to its own server should allow the most accurate evaluation of the current state of that application. Additionally, there are a broad range of vendors who have signed up to support this architecture. This means that, eventually, there will be a rich set of security applications that are Cisco NAC-aware. There are several drawbacks with this distributed approach, too. The job of putting together a real solution will fall on the administrator. There are also a large number of components to the system; each application has its own agent and policy server. Too many components mean too many points of failure — especially at network connection time — reducing the effectiveness of the solution and resulting in more network downtime. From a total cost of ownership perspective, each time the administrator wants to change a policy, they will need to determine which policy server needs to be updated and make the changes there.
Sometimes these policies may also require changes to the Cisco ACS server. All these various server elements will need to be running at all times and responding with minimal latency to endpoint integrity messages in order to avoid impacting users’ network access experience. Also, elements need to be Cisco NAC-aware in order to report their status. If the administrator wants to monitor something without an agent, they will need to rely on another agent that is Cisco NAC-aware in order to do this. Managing several Cisco NACaware components will increase the complexity of maintaining a Cisco-NAC solution. There are also several network-infrastructure-related issues for customers to sort out. The issue of how to support non-Cisco hardware is one of these dilemmas. Cisco has plans to submit some components of the protocols to standards bodies at some time in the future.
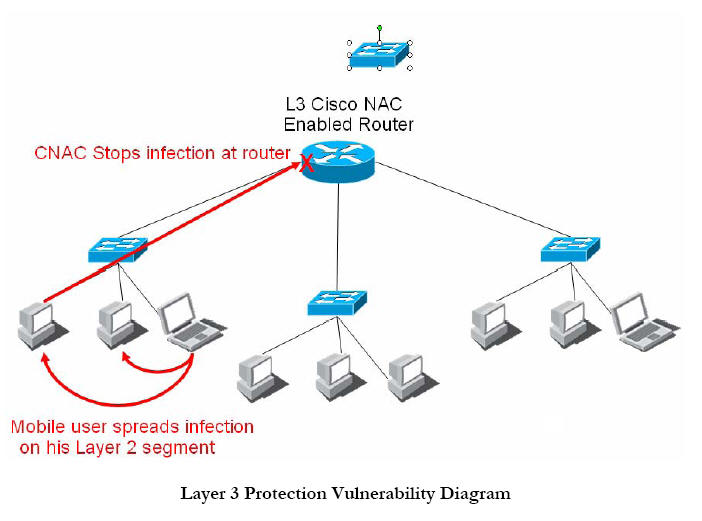
Whether a single standard will be adopted by all vendors remains to be seen. Alternatively, customers can rely on solutions such as Sygate LAN/Gateway Enforcer, which supports multi-vendor network infrastructure. Another infrastructure issue relates more directly to how Cisco NAC works. Today’s protocols enforce compliance at Layer 3 of the TCP/IP stack. In other words, a system’s traffic is not allowed to pass through the first router unless the system is compliant with policy. However, this means that the system can still send traffic on its local LAN segment. This means that a worm can still spread, and infect a large number of systems, even with Cisco NAC in place. In today’s world of hybrid virus/worm attacks, Cisco NAC by itself may do little to stop a threat that uses email to reach a large number of end points in an organization, and then spreads from system to system as a worm. See the figure, “Layer 3 Protection Vulnerability Diagram,” for an illustration of how this works.
Cisco is expected to extend NAC to switches sometime during 2005. This switch-level support will come through proprietary extensions to the 802.1x protocol. This means that customized endpoint 802.1x software will be required, along with firmware upgrades of the switching infrastructure to make it compliant with this new protocol.
Many of these problems can be eliminated by using Sygate’s Compliance on Contact technology, either by itself or in conjunction with Cisco’s Network Admission Control.
Cisco and Sygate Together
Last fall, Sygate Technologies, Inc. became an official Cisco Network Admission Control Technology Partner. Sygate is working to implement Cisco’s NAC protocols in future versions of its products. This partnership gives customers valuable choices when deploying NAC technology. Since Sygate’s NAC solution encompasses all connection points and is completely compatible with Cisco infrastructure, customers can deploy Sygate technology now, without Cisco’s NAC infrastructure. This approach eliminates the complexity of deploying an additional agent — the Cisco Trust Agent — on each system and reduces the complexity of the server back-end infrastructure required.
Customers can also choose to use Cisco’s NAC framework with Sygate’s mature agent and policy server products. Customers who deploy Sygate’s Compliance on Contact technology via Cisco’s NAC transport will enjoy the advantages of Compliance on Contact via enforcement methods available through NAC-enabled components. Advantages include the central administration of security policies and monitoring compliance to overall endpoint security posture. By uniting policy administration in one management console, the entire NAC solution is dramatically simplified, both in terms of deployment complexity and ongoing support. Instead of installing multiple plug-ins on each endpoint and managing separate policy servers for each security element, a single agent and policy server are needed, as shown in the figure below.
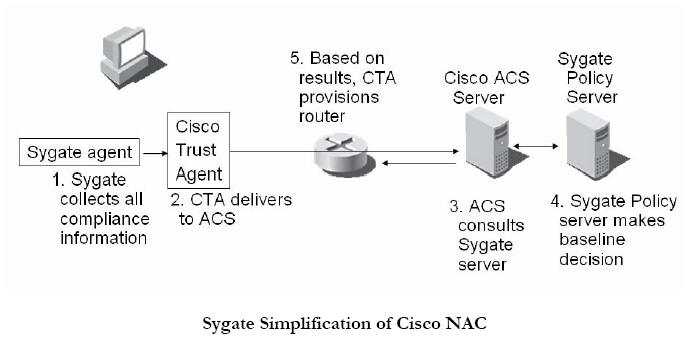
With Sygate Compliance on Contact you get a single solution to protect your network from untrustworthy endpoints and to protect enterprise-owned laptops from untrustworthy networks.
Furthermore, the problem of how to support non-Cisco network infrastructure is also eliminated by the joint Cisco/Sygate solution. Sygate’s LAN Enforcers and central policy management system are designed to be used in mixed environments. Individual endpoints or sections of the network can run any of the various modes of policy enforcement independently of the other sections. This allows almost any type of network infrastructure to be deployed and a consistent set of policies be enforced through the Sygate solution. If Cisco NAC is the preferred network protocol for enforcement, it could be deployed throughout the enterprise, and other enforcement methods (such as API or 802.1x) could be deployed in sections of the LAN where other vendor’s networking equipment exists.
If uniformity of enforcement techniques is desired, Sygate’s API and 802.1x solutions can be used throughout the network, even on the Cisco equipment. In this case, a single solution can be used for NAC compliance throughout the enterprise, as shown in the figure labeled “Typical Best-of-Breed Network,” on 13. The approach any given enterprise should choose will depend on the type of equipment (authentication solutions, switches, VPN, dialup, etc.) they have installed and their own preference of protocols.
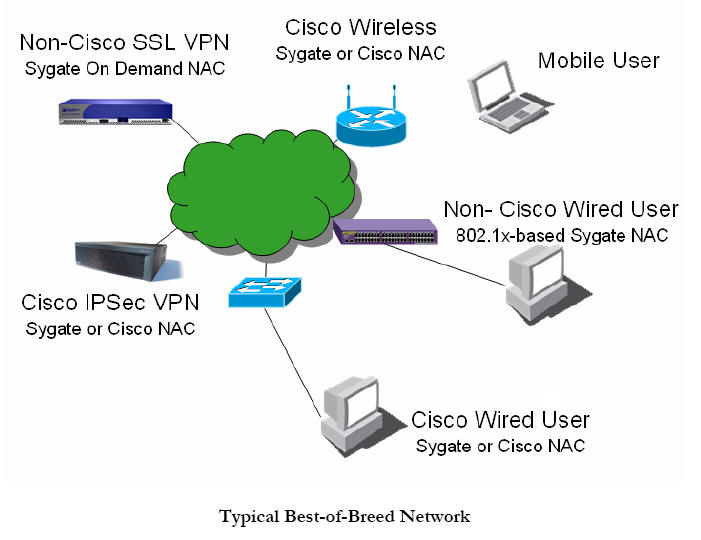
Additionally, customers who have and will deploy Sygate’s self-enforcement, gateway or 802.1x solutions can, at a future time, migrate to using Cisco NAC by simply installing CTA on the client endpoint. Sygate will automatically detect the presence of the CTA agent, and if it is activated, Sygate will deliver all of its status information via Cisco NAC. This means that customers who prefer to use Cisco’s framework for NAC can begin deploying Sygate today, taking advantage of the network protection offered by NAC technology, without worrying about transition issues later.
Microsoft’s Network Access Protection
Microsoft has also weighed in on Network Access Control, with its own Network Access Protection (NAP) architecture. Like the Cisco NAC architecture, NAP is a framework upon which third party vendors can build complete NAC solutions.
From a functional perspective, Microsoft and Cisco have designed very similar frameworks. Each has components that perform similar functions and high level solution diagrams look nearly identical. For example, instead of Cisco Trust Agent, Microsoft has the Quarantine Agent; instead of Cisco ACS radius server, Microsoft has the IAS radius server. Details regarding the compatibility between these two architectures are not available yet, leaving customer without a clear NAC direction. Similarly, vendors of security and antivirus software products must do twice as much work to be able to support both of these frameworks in their products. It is worth noting that Sygate LAN Enforcer today supports both Microsoft IAS and Cisco ACS, enabling the network architects to keep their network architecture intact while introducing/overlaying a NAC framework onto their infrastructure.
One significant difference between the two proposals is their initial method of enforcement. While Cisco is concentrating on Layer 3 network Access Control Lists to enforce policy compliance, Microsoft is concentrating on a network-independent approach using DHCP. In the Microsoft model, a client’s DHCP server will return to the client a different IP address subnet mask and routing table based on the client’s policy compliance. If a system is fully compliant, it will receive a normal, fully-routable IP address from the DHCP server. If it is not compliant, it will receive a DHCP lease with a restricted level of network access, typically including access to a remediation server. Once the system has brought itself up-to-date, it will request full network access and receive a regular network IP address.
Systems that are not NAP-capable will be exempted from the NAP process and receive valid DHCP leases. Systems with statically-configured IP addresses will also be exempted from NAP, since they will never attempt to contact the DHCP server. This means that many systems that are not NAP-capable will be able to spread malicious code throughout the network. These systems that are not NAP-capable are the same systems that are most likely to be compromised, given their older operating systems and lower patch levels.
The Microsoft NAP solution is only expected to support newer Microsoft operating systems, possibly only Windows XP SP2 and above. This presents two implementation problems:
How will older systems, which are often more vulnerable to exploit, be kept off the network if they are not compliant?
How will compliance be ensured for non-Microsoft products?
Microsoft is bundling support for the NAP solution into the Longhorn server operating system, which is expected to ship in very late 2005. Until that time, no production-quality NAP components will be available. So far, over 35 industry companies, including Sygate, have joined Microsoft’s NAP initiative and plan to release products around the time that Longhorn ships in 2007 or later. Much like Sygate’s commitment to support Cisco NAC seamlessly within a Sygate Compliance on Contact network, Sygate will support using NAP side-by-side with our own NAC technologies. Furthermore, users who wish to deploy Sygate today can be assured of a migration path to Sygate’s NAP-based enforcement of policy once Microsoft has released full support.
Trusted Computing Group’s Trusted Network Connect
The Trusted Computing Group, a consortium of over 80 IT industry companies, has sponsored the Trusted Network Connect standard. This standard is similar in intent and architecture to both the Microsoft and Cisco efforts; however, it has been shaped by all of the companies that are part of the consortium, which any company can join. In this way, the TNC specification represents a truly open standard that is intended to operate on any type of network hardware infrastructure and any host operating system. See the figure below for a summary of the components of each architecture.
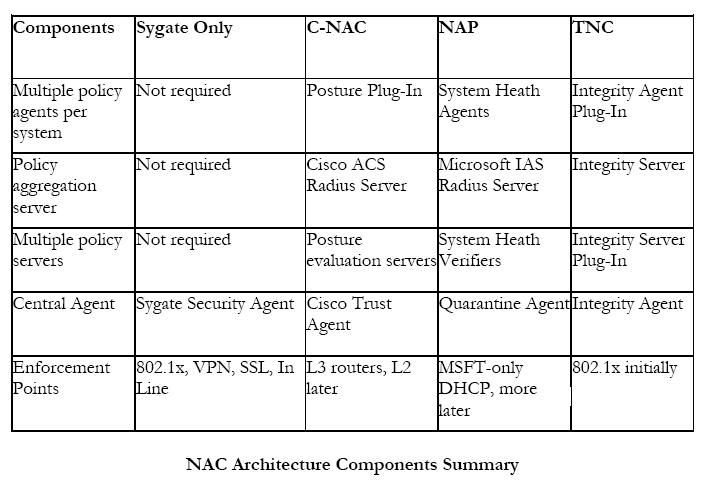
Open standards have been the key to success in the growth of the Internet and IT technologies. An open standard for NAC should encourage the development of NAC agents for other operating systems, either by OS vendors themselves, third parties, or the open source community. A standards-based approach to this problem would also reduce the burden on individual companies wishing to make their products NAC-ready. A single effort would be needed, instead of porting to two or more competing architectures.
The Trusted Computing Group is also responsible for developing the Trusted Platform Module (TPM). This hardware component is used to increase the security and trustworthiness of endpoint computer systems. Many vendors, including HP and IBM, are shipping systems with TPM support today. Ultimately, the TCG will be incorporating support for the Trusted Platform Module (TPM) into the TNC standard.
Once TNC standards include the TPM, corporate IT administrators will be able to determine with much greater certainty that a given computer requesting access to the network is indeed the system it is claiming to be and that the information they are relaying is, in fact, true. The TNC standard is the only one with a roadmap toward ensuring the authenticity of the client/server NAC communication. This will be a big benefit and will increase the security of the network.
The first version of the TNC’s specification is in final review by members today. Vendors are expected to begin supporting TNC functionality in their products late in calendar year 2005.
Conclusion
Network Access Control technology has the promise to dramatically reduce both the number and severity of security events and aid in regulatory compliance. Sygate’s Compliance on Contact technology delivers on the promise of NAC today, enforcing policy via a variety of network protocols and access methods. The breadth of Sygate’s solution, encompassing not only the basics of the NAC solution but also the spectrum of features required to make a solution deployable and scalable, makes Sygate the clear choice for real-world NAC deployments. By partnering with Cisco, Microsoft, and the Trusted Computing Group, Sygate offers a solution that doesn’t make administrators choose between these three architectures, and even allows administrators to use the best elements of each to solve the problem. This further strengthens Sygate’s proven solution that has been deployed in the real world by several Fortune 1000 companies.
Resources
-
Pescatore, Nicolett, and Orans, Protect Your Network with Network Access Control, Gartner, Inc., 2004
-
Cisco, Cisco Network Admission Control:
http://cisco.com/en/US/netsol/ns466/networking_solutions_sub_solution_home.html
-
Microsoft, Microsoft Network Access Protection,
http://www.microsoft.com/windowsserver2003/technologies/networking/nap/default.mspx
-
Trusted Computing Group, Trusted Network Connect,
https://www.trustedcomputinggroup.org/downloads/TNC_NI_collateral_10_may_(2).pdf
Editorial Policy: Nothing you read in The Business Forum Journal should ever be construed to be the opinion of, statements condoned by, or advice from, The Business Forum Institute, its staff, workers, officers, members, directors, sponsors or shareholders. We pass no opinion whatsoever on the content of what we publish, nor do we accept any responsibility for the claims, or any of the statements made, within anything published herein. We merely aim to provide an academic forum and an information sourcing vehicle for the benefit of the business and the academic communities of the Pacific States of America and the World. Therefore, readers must always determine for themselves where the statistics, comments, statements and advice that are published herein are gained from and act, or not act, upon such entirely and always at their own risk. We accept absolutely no liability whatsoever, nor take any responsibility for what anyone does, or does not do, based upon what is published herein, or information gained through the use of links to other web sites included herein. Please refer to our: legal disclaimer
The Business Forum
Beverly Hills, California, United States of AmericaEmail: [email protected]
Graphics by DawsonDesign
Webmaster: bruceclay.com
![]()
�
Copyright The Business Forum Institute - 1982 - 2015 **
All rights reserved.
The Business Forum Institute is not responsible
for
the content of external sites.